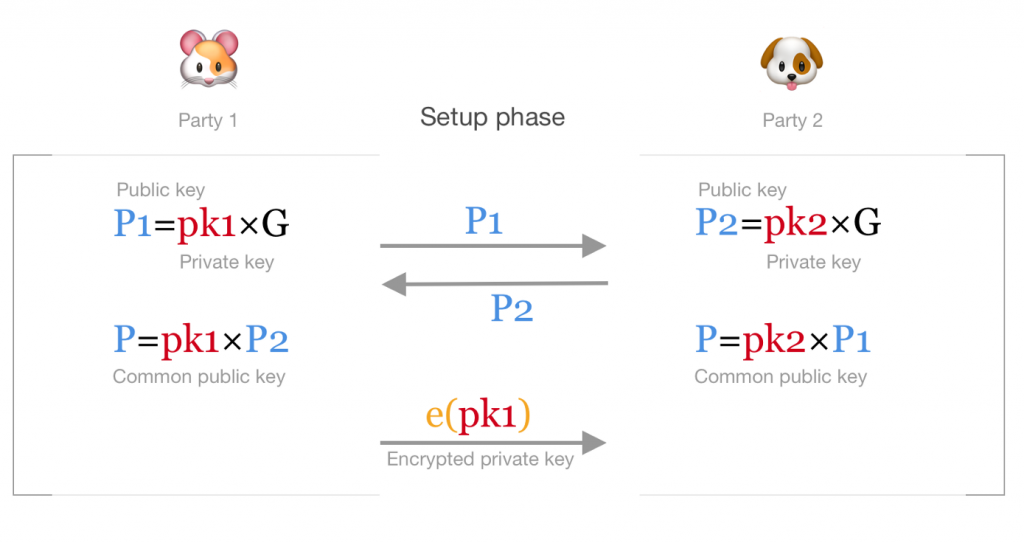
ECDSA is not that bad: two-party signing without Schnorr or BLS
I already wrote about Schnorr and BLS signatures and I think they are really great. One of the most exciting properties of these signature schemes is key aggregation — if we want to make a 2-of-2 multisignature address we just take our public keys and add them together. The signature will be also just a …
ECDSA is not that bad: two-party signing without Schnorr or BLS Read More »
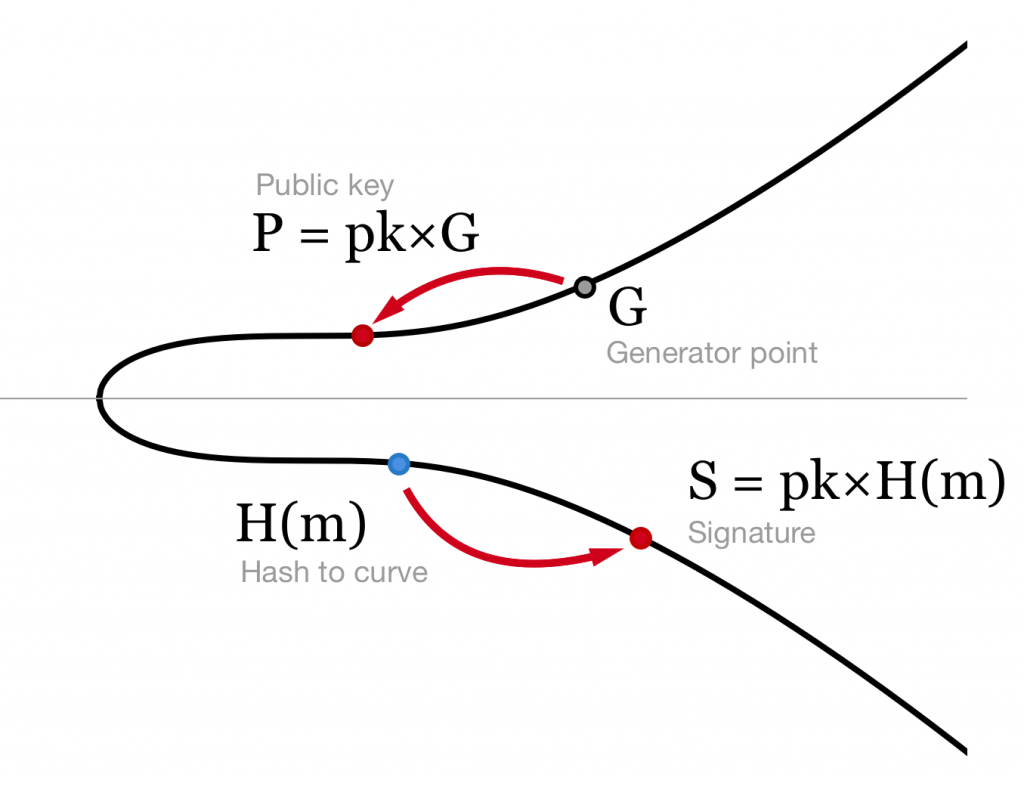
BLS signatures: better than Schnorr
In the previous post I wrote about Schnorr signatures and how awesome they are. This one is about Boneh-Lynn-Shacham signatures and their extremely nice features that are not possible with Schnorr. Shortly, what we know so far: ECDSA signatures are ok. They do their job and do it well, but nothing more. We can’t combine …
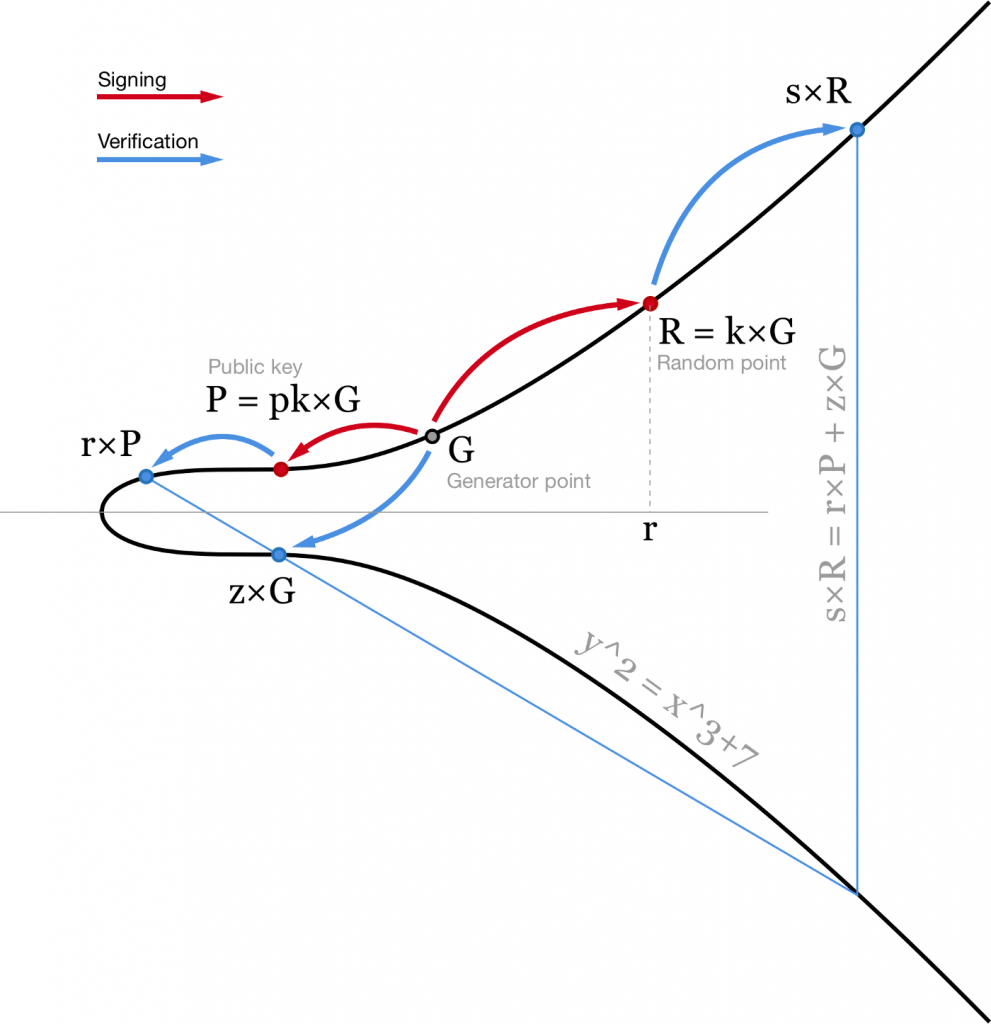
How Schnorr signatures may improve Bitcoin
When I was reading the MuSig paper from Blockstream I was trying to imagine what would it mean for me as a bitcoin user. Some features of the Schnorr signatures I found really great and convenient, but others are pretty annoying. Here I want to share my thoughts with you, but first, a quick recap: …